Ha… I finally got my head around what you and Steve Gibson had been talking about.
Its so opaque when you don’t get what people “who know what they are talking about” are ‘talking about’… its also hard to remember what its like “not recalling how it was when you didn’t know something” when your explaining it… a communications mismatch.
[On the Android phone, including the latest Android 6.0 ‘Marshmallow’]
[Settings… gear icon ] [at the very bottom of the Settings list… is…]
[ {} Developer options ] <= tap to go inside this menu [third item down… is…]
[Enable Bluetooth HCI snoop log ] <= toggle this on by tapping the icon
It says “Capture all bluetooth HCI packets in a file”
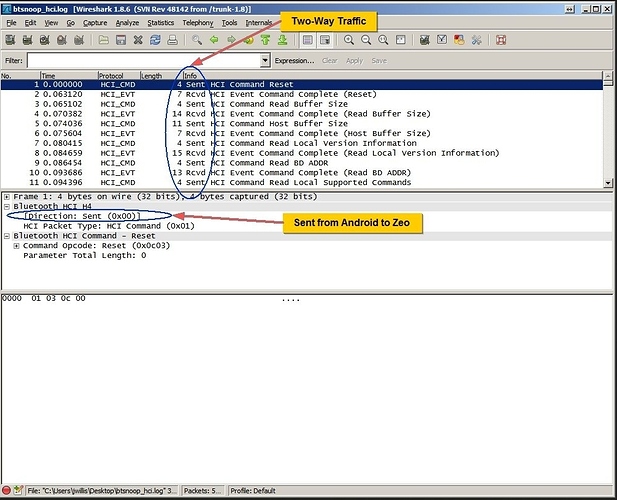
This webpage Wireshark: Bluetooth says HCI_H4 is an encapsulation format that Wireshark understands. But that the early version of the pcap format that Wireshark reads did not support direction information (sent : received) Direction info missing for Bluetooth H4 captures in pcap-format the bug was filed in 2007 and fixed by 2008.
Since Android 2.2 Froyo was released in 2010 that bug predates current versions of Android by quite a bit. It would suggest that perhaps later versions of Android did include the fix, and that the information is there… maybe your saying the current dissector “direction” bug is in the current implementation of the overall dissector in Wireshark, or the recent Zeo protocol wireshark plugin you just created. “I am not quite sure which you meant… or if you have enough information to know where the bug is for sure at this point.”
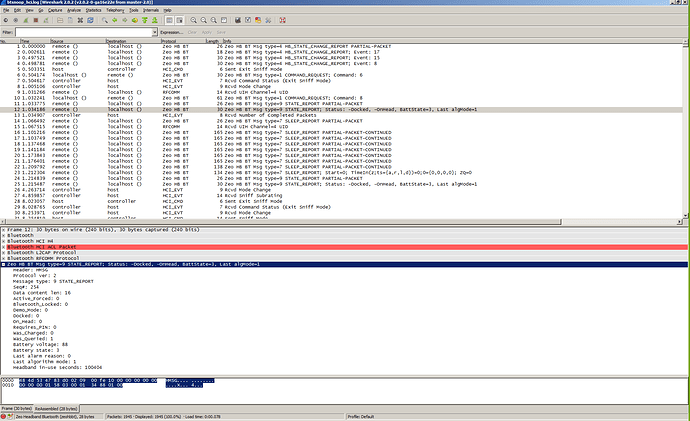
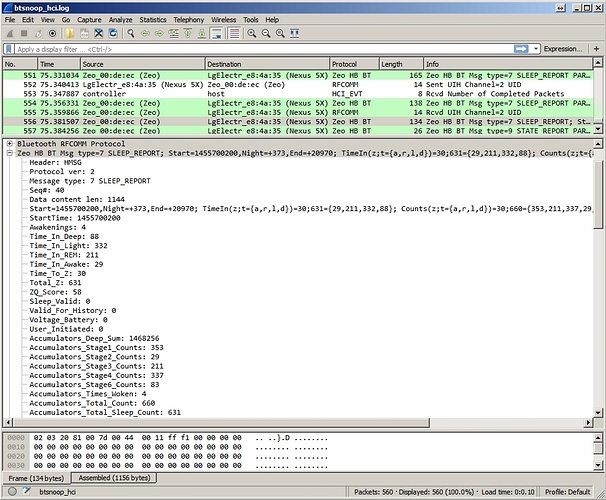
I took a more pedantic direction and put together a simple Rfcomm service and screen dump… skipping all the protocol layers up to the raw data. “But” that obviously means I did not have a tool to cleanly and neatly dissect and interpret the messages and produce nice neat back and forth streams.
This approach is indeed “Faster”.
There is another generic Windows binary stream parsing tool I was thinking of using called “Hexinator”… but not as well known… and there are others… but I like this one better… Wireshark is more universally available on many platforms.
From this site 32 things you can do in Android Developer Options I see the Android device Bluetooth log can be found in /sdcard/btsnoop_hci.log
That now matches up with what you said,
"Just use the Android Developer Mode Bluetooth HCI snoop feature on the device, then pull the log file off the device… "
Not sure about
" … force a “Decode as” for the RFCOMM…
But I’ll figure it out
" … put the LUA script (on Windows) into “C:\Users\jwillis\AppData\Roaming\Wireshark\plugins”
Seemed to be correct for me, interpreting the path for my username
I got an error message loading the LUA however while starting
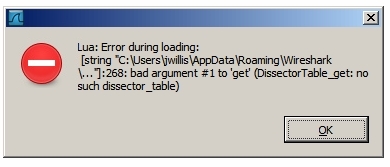
It could be the exact version of Wireshark I am running… currently
[Version 1.8.6 SVN Rev 48142 from trunk-1.8] needs to be updated.
I’m away from my test environment… so while I have my Android device with me… I don’t have the Zeo with me. I should have a lot more time to capture Bluetooth HCI packets this evening.
I’ve been using a lot of these tools for years… but never deep dived into Bluetooth or used Android debug or Wireshark in this particular manner… so my ‘learning curve’ could be entirely slow and frustrating for those who do this a lot more. It would be entirely understandable.
But nothing tried, nothing gained… and this is really interesting